I worked really hard in designing the Windows-as-a-Service at my workplace. It’s been a great learning experience full of engineering and automation experience. A lot of superstars in the tech community have posted their upgrade task sequences and scripts and I wanted to write a post of my own specifically to demonstrate the user experience in the upgrade process.
What I have here is basically the guidance we’ve provided to our own staff which is perfect for the purpose of this post.
Introduction
Following our previous update, we’ve had a very successful run of the upgrade during our pilot phase and are now ready to roll this out to the rest of the organisation.
The Windows 10 1909 Upgrade should be available to your device shortly; this will appear in the Software Centre. You will get a prompt advising you when the installation is ready. This is what it looks like:
When the upgrade is available for your device you will initially be notified by this prompt:
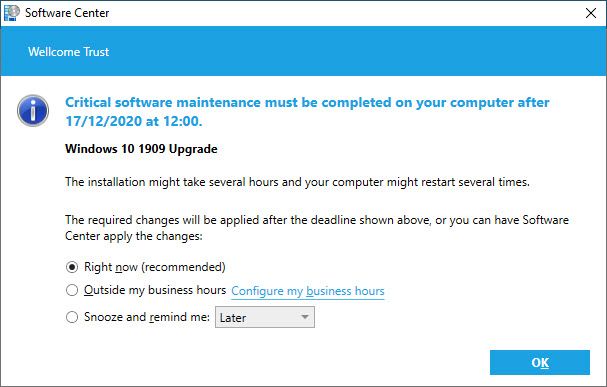
Install Reminders
You can either upgrade straight away if it is convenient for you or you can snooze the upgrade.
You will also be prompted every 2-3 hours reminding you that the upgrade is available for you to install. This will include instructions for you to follow and the deadline for the upgrade.
An example of this prompt is provided below:
Once you see this you can either go directly to Software Center from this window or follow the instructions below.
Deadline date: Please note that you will be given a deadline date to run this upgrade; if you fail to upgrade by this time, your system will perform a forced upgrade, which may cause interruption. Therefore, to prevent this we recommend you run this upgrade at your earliest convenience.
Before you upgrade: make sure your laptop charger is plugged in and Global Protect is connected.
Instructions on how to install the upgrade:
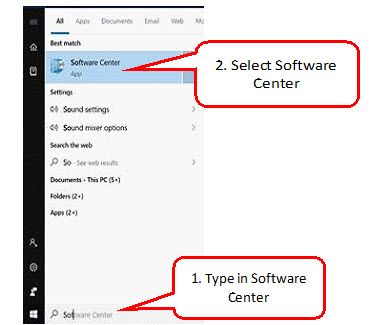
1. Open Software Center from the Start menu (or type it into search bar once you click start).
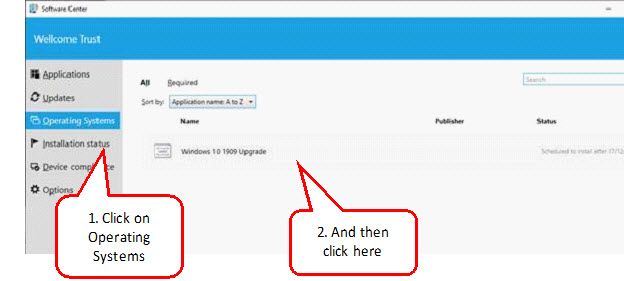
2. Click on the “Operating Systems” tab. You will see “Windows 10 1909 Upgrade” listed here.
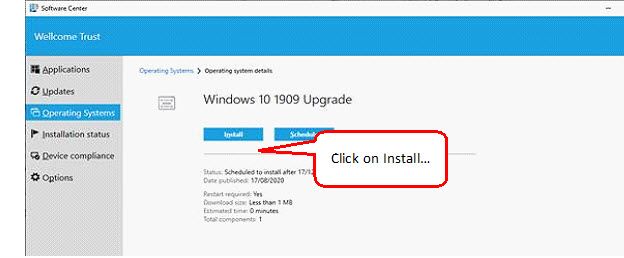
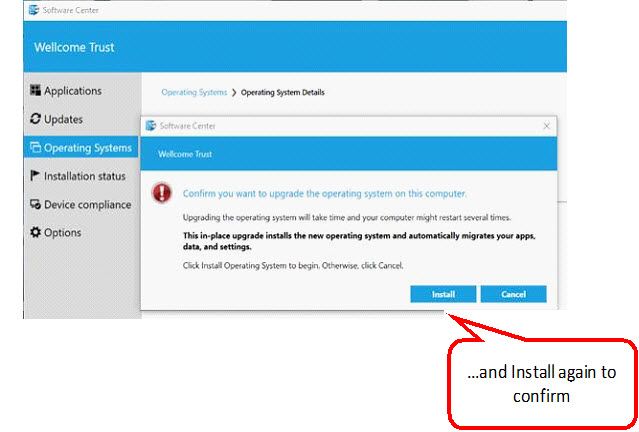
3. Click on the ‘Install’’ button and confirm installation by clicking Install again.
Confirm installation
4. Software Center will then close automatically – do not be concerned by this, rest assured the upgrade will continue in the background.
Please do not unplug the charger and remain connected via Global Protect.
Note: It is recommended to start the upgrade at the end of the day or during lunch break and walk away to allow the upgrade to continue without any interruptions.
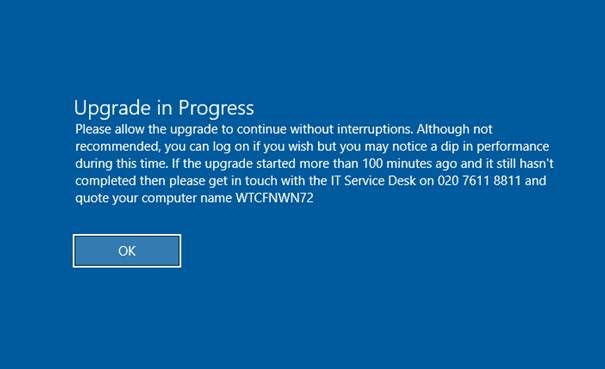
You will see a message on the lock screen advising you that an upgrade is in progress. Although not recommended. you can log back in again if you wish but please do not restart or shut down the computer until you are prompted to do so as mentioned below.
This is what the upgrade process will entail:
-
Installation will take place in the background and will take just over 90 minutes.
-
If working from home it is recommended to install the upgrade at the end of the day and walk away so the upgrade can continue without interruptions.
-
Once install has completed you will be prompted to restart your computer with a 15-minute countdown.
-
When prompted please close all open applications and click on the ‘Restart Now’ button.
-
If you do not click on “Restart Now” within the 15 minute window the computer will forcefully restart. Please DO NOT restart the computer using the power button or from the Start menu but instead click on ‘Restart Now’ in the prompt that will be displayed.
-
Your computer will restart and finish installing the upgrade. This part will take roughly 30 minutes during which you will not be able to log on. It is normal for the computer to restart a couple of times during this stage.
-
Once the lock screen displays a message that the upgrade was successful you can go ahead and log on. The first log on after the upgrade will take a couple of minutes longer than usual.
If you sign out or lock your computer:
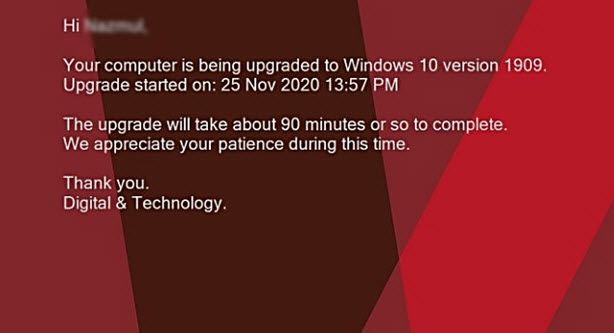
You will see a message on the lock screen advising you that an upgrade is in progress which will look like this:
You can log back in again and continue working. You’ll see this message when logging on while the upgrade is in progress:
You can continue working until you see a prompt to restart as mentioned earlier.
When the upgrade is complete:
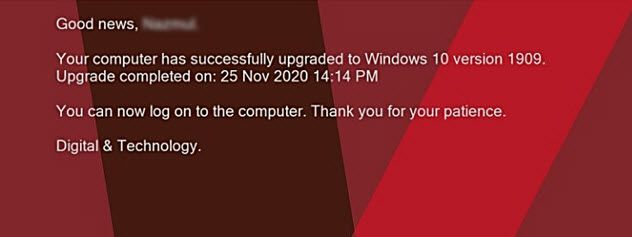
The message on the lock screen will change to say the upgrade finished successfully as shown below:
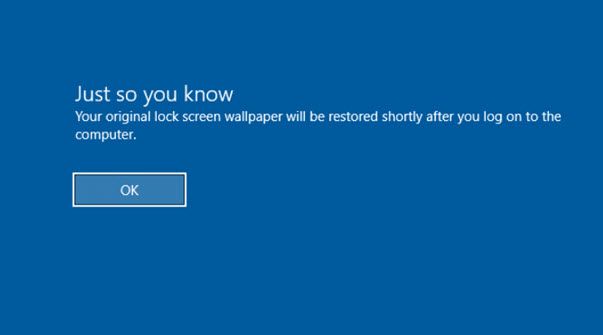
And when logging on you will see a message to say that your original lock screen wallpaper will be restored:
Further support & information:
-
If the computer failed to upgrade, the lock screen wallpaper will display a message. You will still be able to login in and continue to work, despite the upgrade failure.
-
If this happens, please raise a ticket with Service Desk with ‘Windows10 upgrade fail’ in the subject line along with your device service tag in the description.
-
A member of the D&T team will be in touch, advising you of the failure and how to re-start the installation.