So in the last post we stopped at the point of creating additional users who you want to give VPN access to. I also explained that the connection from the RRAS server to the OpenVPN Cloud counts as 1 out of 3 connections so you are left with two connections for your endpoints/users.
Now let’s get the connector installed on our endpoint device and our users connected.
Just a quick reminder that the portal address is “youropenvpncloudId.openvpn.com”
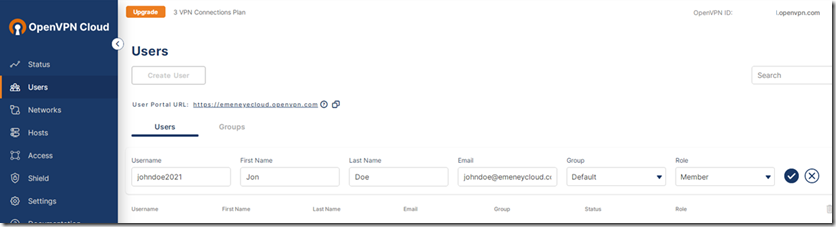
1) Log into your OpenVPN web portal and add your end users. Note that the email address here must be valid for this to work. Since this is intended for lab use just enter your own for testing.
2) Build a VM with Windows 10 installed. The virtual network adapter must be connected to the Internal switch to join the domain and verify you can ping the domain and maybe access a file share or something.
3) Now change the virtual network adapter so it’s bound to the External switch instead to simulate offsite access. Verify that you cannot ping the domain.
4) On this VM log into the email address you provided for the user which has instructions on how to install the connector app. It’s just a standard MSI so go ahead and install it.
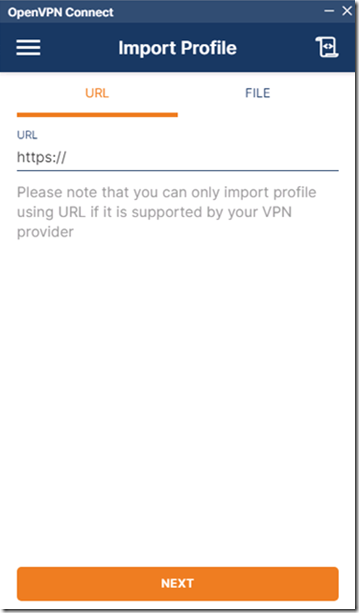
5) Open the connector app and enter your OpenVPN Cloud portal URL.
Sign in with the user account ID you created earlier.
Choose your Region and click Connect. It should only take a few seconds to establish the VPN connection.
Verify that you can ping your domain and access file shares.
You can, of course, install the endpoint connector on a physical domain-joined laptop and connect to your Wi-Fi (assuming your lab is on a Internal/Private network) to test this.
In the next post I will go through instructions on how to enable Azure SSO so you don’t have to manually create the user accounts in the portal and better simulate a production environment.
![image_thumb[10] image_thumb[10]](https://emeneye.files.wordpress.com/2021/08/image_thumb10_thumb.png?w=836&h=227)